Cloud computing1 is the gold standard operational model and set of technologies for managing shared pools of computing resources. It is a disruptive technology that has the potential to enhance collaboration, agility, scaling, and accessibility, as well as provide the opportunities for cost reduction through optimized and efficient computing.
The ideal cloud model empowers you to, rapidly orchestrate, provision, implement and decommission components, scaled up or down to provide an on-demand utility-like model of allocation and consumpton.
While all this is positive, we must not neglect the security aspect of the cloud.
Safeguarding your data
Unfortunately, there seems to be a tendency that you, the enterprise consumer of cloud services, do not need to worry about cyber security, and that your data is safe, as long as it is in the hands of the cloud provider – be it private-, public- or hybrid cloud setups2.
This is not entirely true.
Going straight to the core, data is both the king and queen on a chessboard, i.e., it is always the most valuable item we have in our cloud stack, and therefore, requires the most safeguarding.
Safeguarding should be achieved by:
- knowing your setup with the cloud vendor, and what arrangement you are entering into (or already have) with your cloud provider and operator, specifically who owns what areas of the security model, and the inherent responsibility, risk and ownership you are looking into.
- knowing the cyber threats relevant for your specific cloud deployment- and service model
- building the layered security approach3, while enforcing the least-privilege principle4
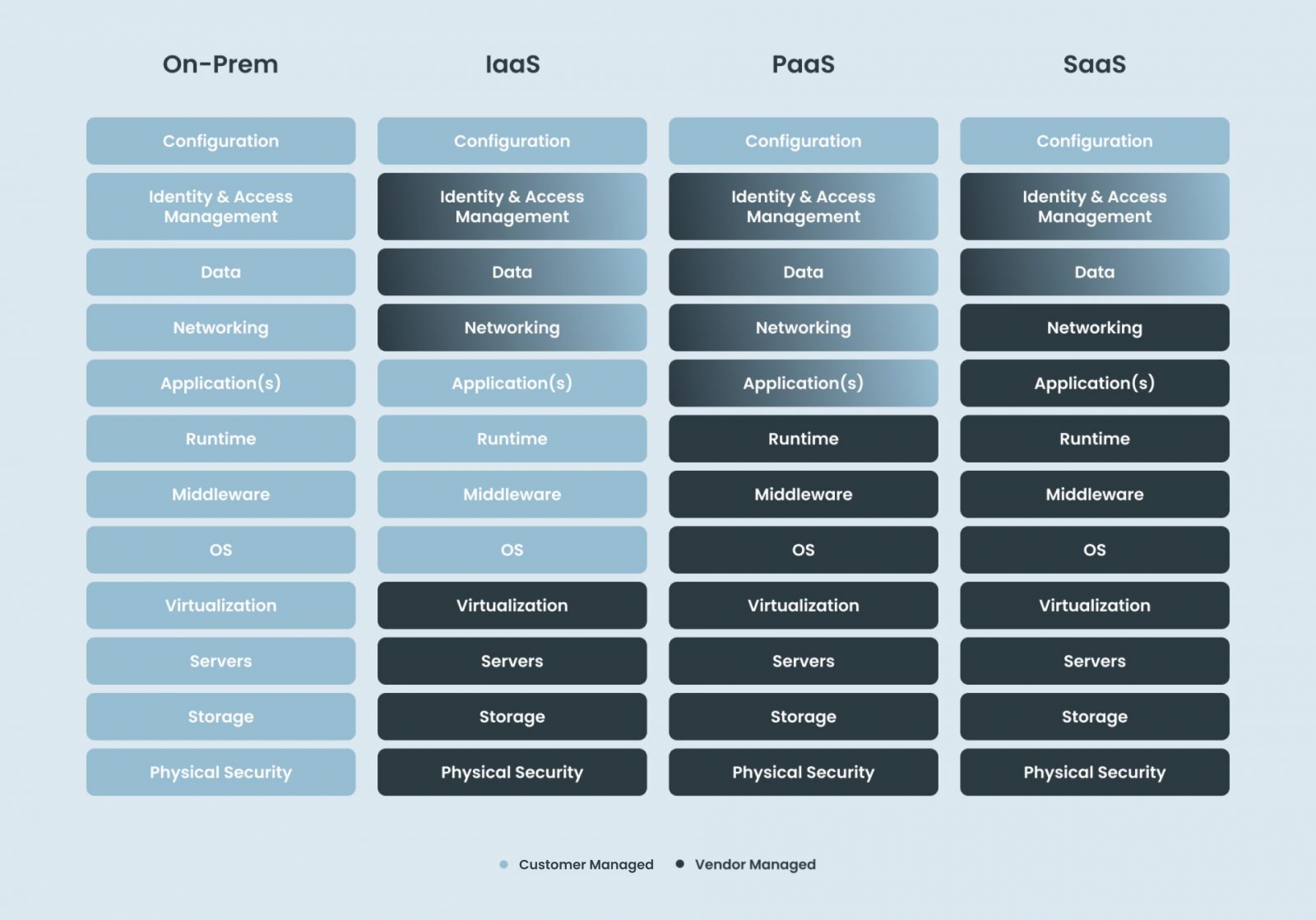
What can you do to ensure you are in control?
The key parameters to cloud security within an organization is to ensure you are in control and ready to make informed decisions. Here is what to look out for within your cloud deployment model and service model:
- Which party owns and governs cyber security of each layer within the cloud model (see ‘Service Model’ figure above), and what does the ownership and governance specifically include – and more importantly, what it excludes
- What security controls does the cloud vendor apply to each of the layers within the cloud stack
- How does the cloud vendor measure success: what KPIs- and KRIs does the cloud vendor apply to each of the layers within the cloud stack (including, but not limited to, capabilities and transparency around detection and response, patch and vulnerability handling, service continuity plans)?
- Lastly, but most importantly, clarify and align internally within your own organization how big your requirements are towards the vendor, but also the amount of requirements you are willing to put onto your own organization – whether you are in the driver’s seat or share the responsibility with the vendor and/or operator
The most crucial security consideration is knowing exactly who is responsible for what in any given cloud initiative between a cloud provider and consumer.
- According to the International Organization for Standardization (ISO), cloud computing is defined as “Paradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand”.
- To read more about the different deployment models: National Institute of Standards and Technology, 2011, SP 800-145 The NIST Definition of Cloud Computing, accessed 28 June 2022, https://csrc.nist.gov/publications/detail/sp/800-145/final
- IBM, 2021, The layered defense approach to security, accessed 28 June 2022, https://www.ibm.com/docs/en/i/7.3?topic=security-layered-defense-approach
- CERT NZ, 2022, New Zealand Government, Principle of least privilege, accessed 28 June 2022, https://www.cert.govt.nz/it-specialists/critical-controls/principle-of-least-privilege/
- Cybersecurity & Infrastructure Security Agency, 2021, US-DoD, Cloud Security Technical Reference Architecture, accessed 28 June 2022, https://www.cisa.gov/cloud-security-technical-reference-architecture
Latest articles & Updates