The cyber threat landscape has evolved and so has the risk
Looking a few years back a number of areas have been evolving in cyber. We have gone from a core financially motivated agenda into an equally political agenda. Additionally, we are as human beings digitizing more and more of our lives across both companies, personal and intellectual property around us. This is a clear call for action to revise how we do security, both at an industry specific level as well as a customer specific level.
Threats are becoming more imminent both internal and external
It doesn’t take much threat research to identify that the ransomware risk is as high as ever, but being able to make informed decisions based on your specific operating environment and your business-critical assets and the threat landscape within your organization is a much more challenging task.
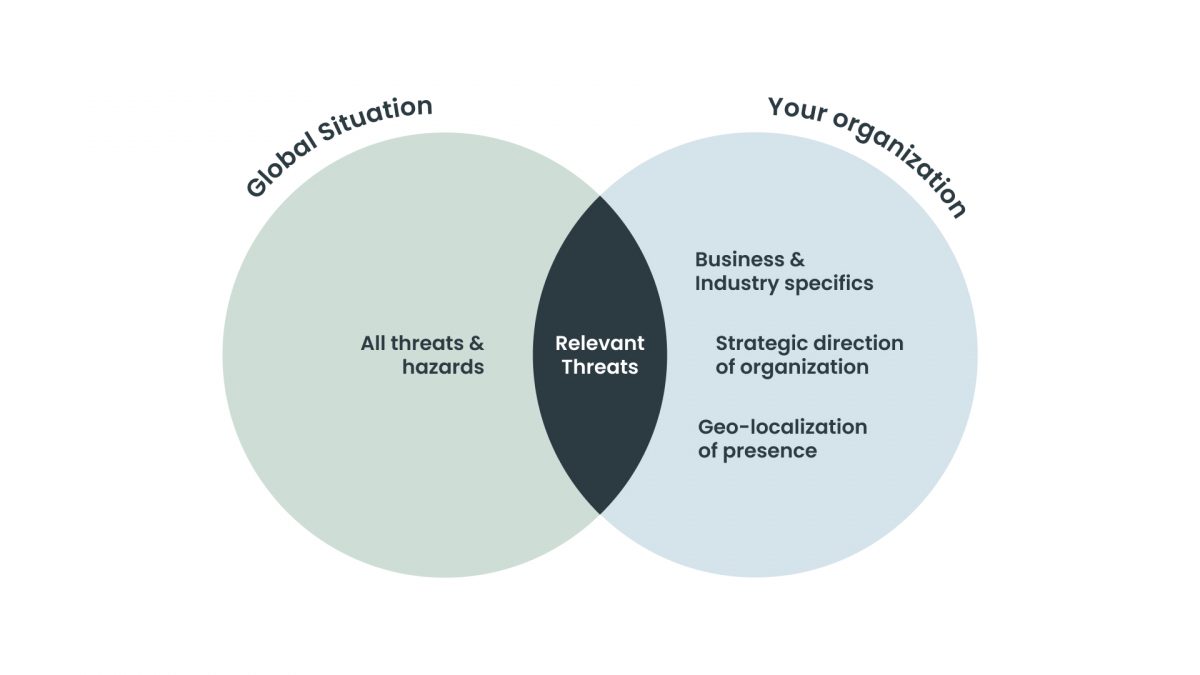
To make informed decisions, it is imperative that your organization is able to initially focus on the relevant threats, as well as deselecting the irrelevant threats and their scenarios. Hereafter it is imperative that the organization is able to build a strategic view across the relevant threats, and their attack way-of-work – i.e. patterns regarding tactics, techniques and procedures of the adversaries, as well as -motives & incentives of the malicious actors (endgame targets).
To do so, you need to not only investigate the technical capabilities of malicious actors, but also analyze relevant data holistically across open- and closed data sources, consisting of learnings from previous attacks within your primarily operating segment – both prevented attacks and successful attacks (from minor to critical incidents) through post-incident intel including extracted indicators of attack (IOAs) and indicators of compromise (IOCs), tendencies and business/industry trends, intel from trusted partners, et al. across sectors and business areas.
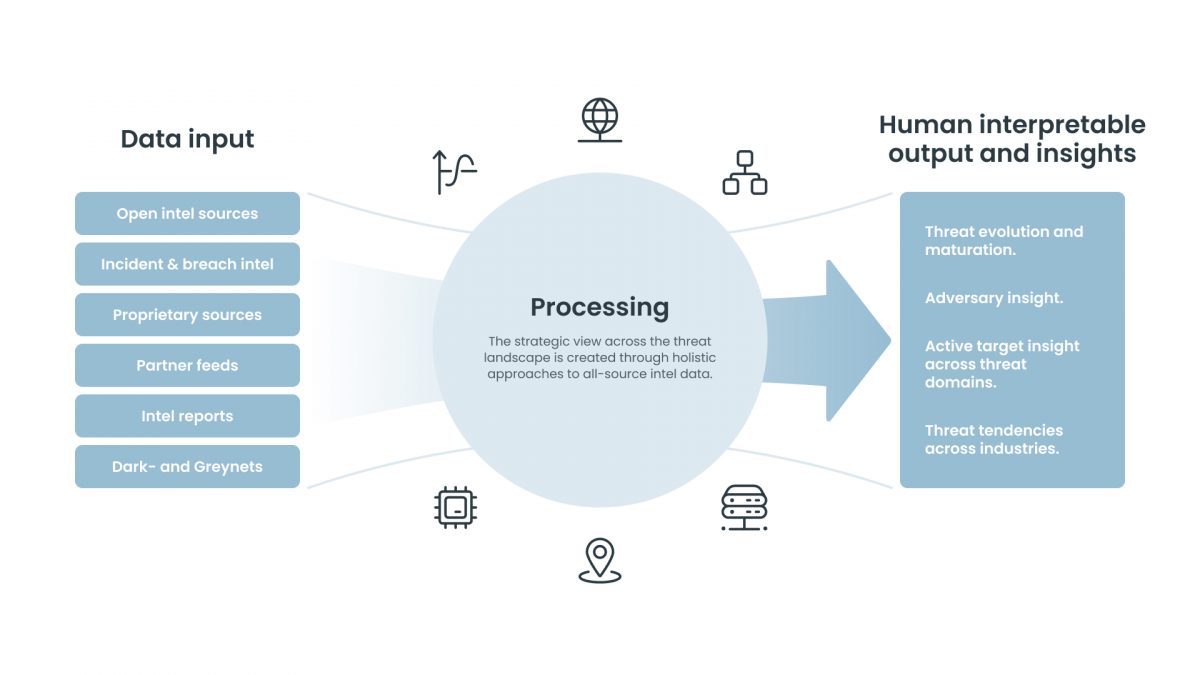
As an example, we have gathered insights on darknet, correlated with intel through trusted partners, indicating known malicious actors seeking to exploit and pivot off of insider threats and disgruntled employees of western-European and Nordic tech companies. The malicious threat actors are offering up to €100.000 for adding a few lines of code in to the core systems of the organizations they work for. Code that could be damaging in a way that potentially could threat the existence of a company monetarily or otherwise.

Shifting gear across people, processes, and technology reduce cyber risk
Trifork has spotted a need in terms of both tech, process and human level in the space. It’s crucial that each company identify where the risks are, and how to mitigate and handle each risk. If you sum everything up, it’s about gaining control. Each organization needs to clarify; where are we in control and where are we not in control? And if you’re not in control, what is the impact upon attack? In the event that the risk is materialized – are you ready to navigate in the evolved cyber reality?
Business-critical cyber transformation
With the current situation in mind, we have developed The Cyber Transformation Model. This model helps organizations prepare for the risks described previously. The model helps organizations make informed decisions and take back control across the cyber agenda.

To empower the decision-makers at Trifork’s customers, we utilize the Cyber Transformation Model to create vantage views of their Cyber capabilities- and the applicable threat landscape. This supports our customer’s executive-level in ensuring the right decisions is taken, at the right time, within set budget frame and -risk appetite, providing detailed feedback on specific target states of relevant security measures, effectively being capable of combatting relevant threat scenarios within the Cyber agenda, all while presenting you an opportunity to extrapolate your execution-power to reach set goals. Everything is finetuned as according to your risk appetite, financial capacity and –maneuverability.
Latest articles & Updates