We match your organisation's ambitions based on your willingness to take risks, your budget, and how long you can stand still. We show you how to handle possible threats and help you make informed decisions.
We match your organisation's ambitions based on your willingness to take risks, your budget, and how long you can stand still. We show you how to handle possible threats and help you make informed decisions.
Your IT security is our top priority. We advise, implement and manage on cyber security, while protecting your data at all costs and minimizing the risk of security breaches.
We uphold the standards of confidentiality, integrity, and availability of information as we understand how crucial they are to the operation of any business and we actively bridge the gap between governance and technology, ensuring that you are in control of your data.
Cyber security is not only a matter of protecting the integrity of systems infrastructure and applications, it permeates the entire organization – from data loss on numerous devices, in different clouds, and even on-premises.

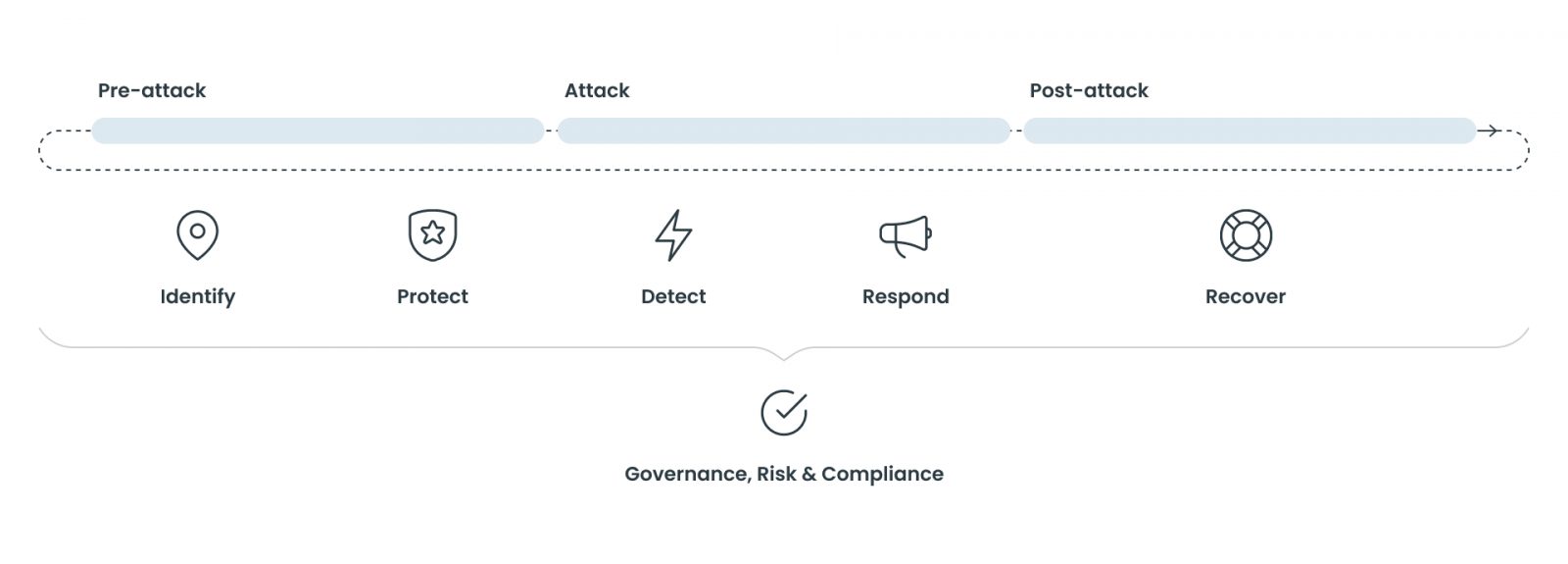
We handle all challenges across all stages of a cyber attack’s lifecycle, from pre-attacks to recovery. We identify and protect your company before any attacks even happen.
We help you detect the attack and respond if you have already been under attack. But if it is already too late, you can come to us, and we will help you recover.
We apply a set of interrelated steps that our customers utilize to manage the risk of cybersecurity incidents. We service our customers across the entire Cyberattack-lifecycle; from pre-attack, during an attack and post an attack, and includes 6 subcategories:
Identify
Business & organisational understanding from a Cyber-perspective, as well as identification of assets and business critical services.
Protect
Implement capabilities to support the ability to limit or contain the impact of a potential cybersecurity event
Detect
Implement the appropriate activities to identify the occurrence of a cybersecurity event.
Responding
Implement activities to take action regarding a detected cybersecurity event (this also includes containment of the incident actively containing the business impact).
Recovering from incidents
Implement activities to maintain plans for resilience and to restore any business capacity, system or service that were impaired due to a cybersecurity event.
Governance, Risk & compliance
Capabilities that establish a clear direction of travel on cyber as well as the necessary structures reporting, managing & handling on a management level.
Latest News
Contact
If you prefer, you can also contact us on info@trifork.com
Subscribe
Find out the latest news first
Content